This is Myeongjae Lee (MJ), back with our report on running the LINE Security Bug Bounty program from January till June this year. The 'LINE Security Bug Bounty Program' aims to provide LINE users the most secure service by fixing potential vulnerabilities in advance, by getting reports from external security researchers.
If you are interested in participating in the program, check out the following links:
- Reporting form (requires signing in)
- Terms of use
- Program FAQ
Submissions
Here is the information of the reports we received in the first half of 2018.
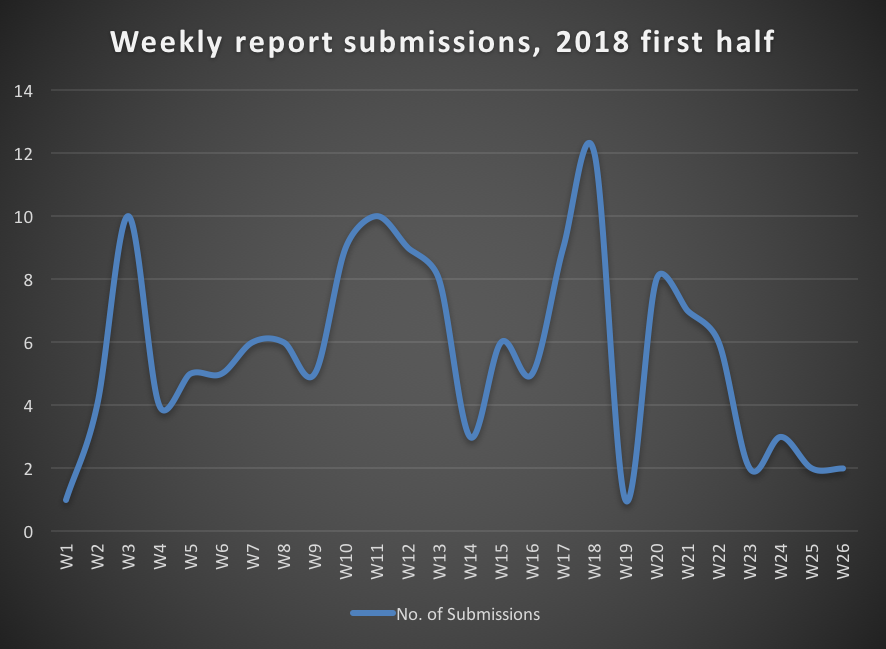
Weekly submissions
In the first half of 2018, we've received a sum of 148 reports. The number of report submissions have increased by 64% compared to the first half of 2017, during which 96 reports had been submitted. You can see the weekly submissions in the following graph.
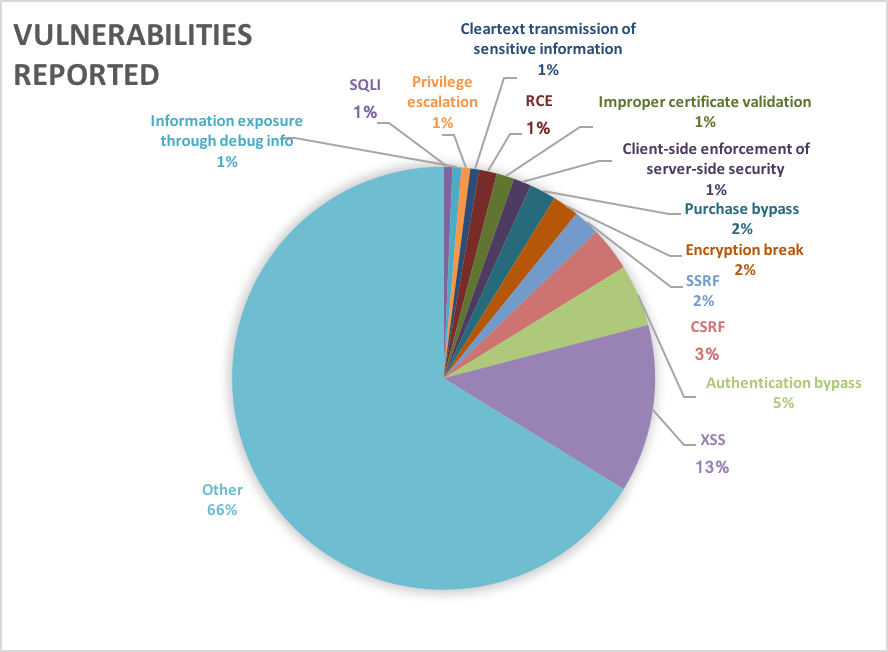
Vulnerability Types
During the period, the types of vulnerabilities reported are as follows:
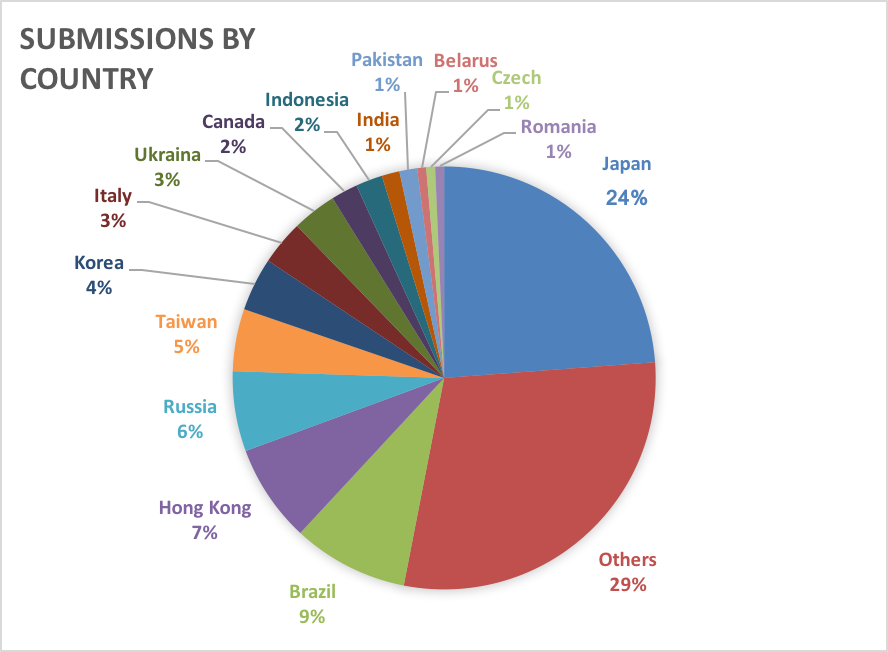
Submissions by country
Of the 148 reports we received in the first half of 2018, 6 reports were from Korea, 35 were from Japan, and the rest were from other countries. The following graph shows the ratio of submissions made by country.
Report evaluation
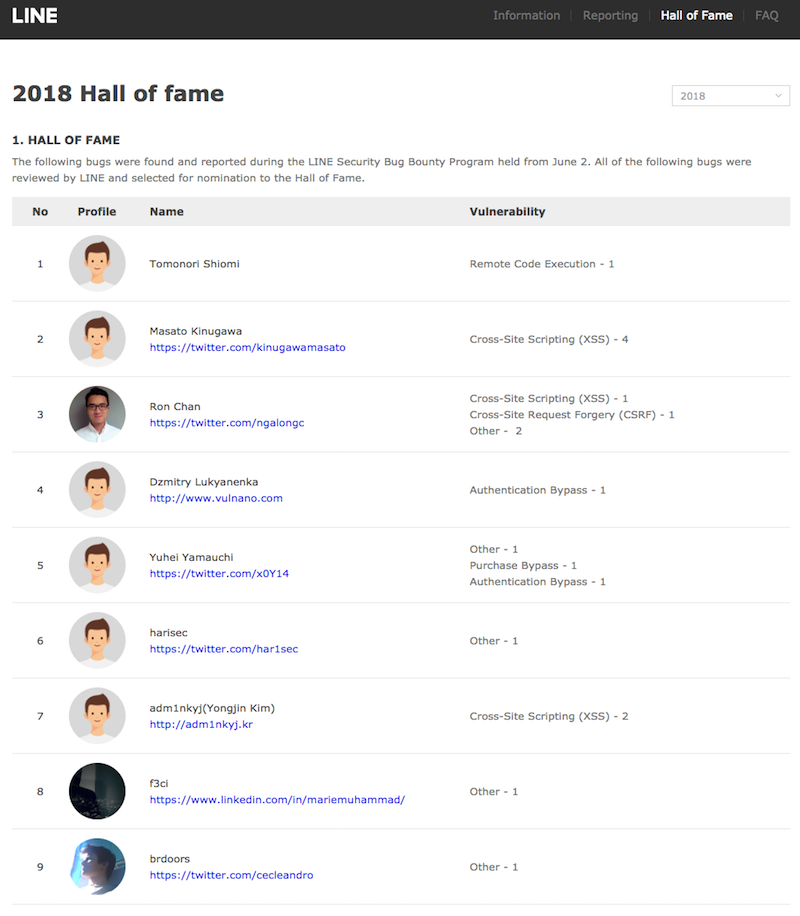
In this round, a total of 33 vulnerabilities, including XSS (Cross-site Scripting) and CSRF (Cross-Site Request Forgery), have been acknowledged. The result can be found on the Hall of fame page and the updates on the page is listed here.
As for the reward, a total of $48,000 (USD) were paid out and here is the ratio of rewards given out per country.
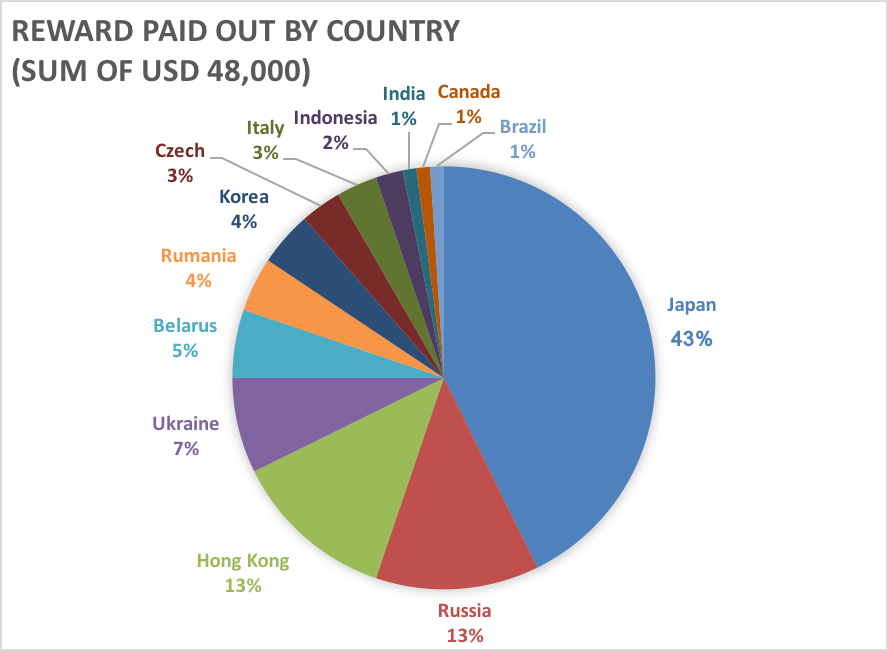
As a result of evaluation, the reports ineligible for official acknowledgement based on the program's terms but are meaningful and helpful to LINE have been rewarded as special contributors. This time, we rewarded 11 special contributors.
Rewards
Reward statistics
| 2018 (Reward table renewal) |
2017 (Program scope expansion) |
2016 (Official launch) |
2015 (Trial) |
|
|---|---|---|---|---|
| Operation period | Jan 1–Jun 30 | Jan 1–Dec 31 | Jun 2-Dec 31 | Aug 24–Sep 23 |
| Report submissions | 148 (Japan: 35, Others: 113) |
212 (Japan: 11, Others: 201) |
97 (Japan: 15, Others: 82) |
194 (Japan: 89, Others: 105) |
| No. of acknowledged vulnerabilities | 33 | 45 | 13 | 14 |
| Hall of Fame | 9 | 11 | 3 | 8 |
| Special Contributors | 11 | 21 | 8 | 9 |
| Total reward | USD 48,000 | USD 76,500 | USD 27,000 | USD 44,000 |
Reward payout process
If a bug reported is acknowledged as a vulnerability, the reporter gets rewarded in the following process:
- A reporter submits a bug report.
- LINE evaluates the bug.
- If the bug is acknowledged as a vulnerability, LINE contacts the reporter regarding the reward.
- The reporter agrees to receive the reward.
- The reporter submits information required for receiving the reward.
- LINE checks the submitted information and documents.
- LINE pays the reward to the reporter.
The average time taken from the report submission and to contacting the rewardee—steps 1 to 3—was 10 days. From notification to the actual payout—steps 3 to 7—took 41 days in average. In 2017, the average time taken for the payout after notifying the rewardee was 52 days. For detailed information on the reward process, see the Q12 on the FAQ.
Reward table renewal
On March 19, as an improvement to the program, the reward table was updated as we twitted here (Note: The content is in Japanese). The following vulnerabilities had been added in. For detailed information, see the terms of use.
Reward Table
|
Vulnerability |
Description |
Reward Reference |
|
Authentication Bypass |
Ability to masquerade as another person by bypassing authentication procedures |
USD 5,000 |
|
Cleartext Transmission of Sensitive Information |
Ability to eavesdrop sensitive information in the network traffic. |
USD 500- |
|
Client-Side Enforcement of Server-Side Security |
Ability to bypass protection mechanism by relying on the client side protection only. |
USD 500 |
|
Cross-Site Request Forgery (CSRF) |
Ability to force a LINE user to perform an undesired process through a CSRF attack |
USD 500 |
|
Cross-Site Scripting (XSS) |
Ability to hijack a session or execute scripts through an XSS attack |
USD 500- |
|
Encryption Break |
Ability to obtain another person's authentication information by cracking encrypted data |
USD 10,000 |
|
Improper Access Control |
Ability to access originally non-public pages because of access control failure. |
USD 500- |
|
Improper Certificate Validation |
Ability to obtain sensitive information by failing to validate SSL certificate. |
USD 10,000 |
|
Information Exposure Through Debug Information |
Ability to obtain sensitive information through debugging information. |
USD 500 |
|
Insecure Direct Object Reference (IDOR) |
Ability to bypass authorization and access resources directly by modifying the value of a parameter. |
USD 5,000 |
|
Other |
Other vulnerabilities |
USD 500 |
|
Password in Configuration File |
Ability to obtain a password or sensitive information in a configuration file. |
USD 500 |
|
Path Traversal |
Ability to access arbitrary files and directories by manipulating variables |
USD 500- |
|
Privilege Escalation |
Ability to obtain elevated access to resources that are normally protected from an application or user. |
USD 3,000 |
|
Purchase Bypass |
Ability to obtain items while bypassing in-app payment procedures |
USD 5,000 |
|
Remote Code Execution |
Ability to send packets containing arbitrary code to the client or server side |
USD 10,000 |
|
Server-Side Request Forgery (SSRF) |
Ability to abuse functionality on the server to read or update internal resources. |
USD 2,500 |
|
SQL Injection |
Ability to access private information through an SQL injection attack |
USD 3,000 |
References
We'd like to share a couple of references for those who have a general interest in security.
Google Play Security Reward Program
Google Play Security Reward Program is a bonus bounty program by Google Play for popular Android apps on Google Play. If you have been rewarded for a vulnerability you've reported to us at LINE, and if the vulnerability is eligible by the Google Play Security Reward Program, you can get rewarded the same amount of bonus bounty by Google by proving that you've been rewarded by LINE. LINE is also a participant of the Google's program.
IETF's proposal - security.txt
IEFT has proposed a guide, Security.txt, for security researches to report security risks. Based on the guide, LINE has uploaded our own security.txt which can be found at the following links:
The files are only drafts, but we wanted to guide our reporters, so here they are.
Ending notes
Thanks to you, we've seen an increase in the number of reward payouts and the amount of reward given out, compared to 2017, and we were able to provide a safer and better service to our users.
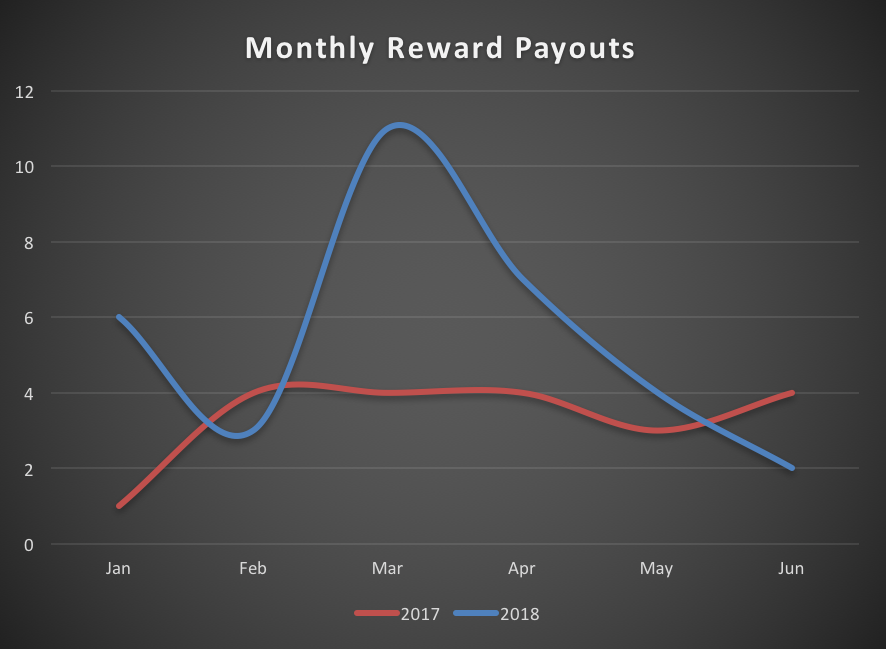
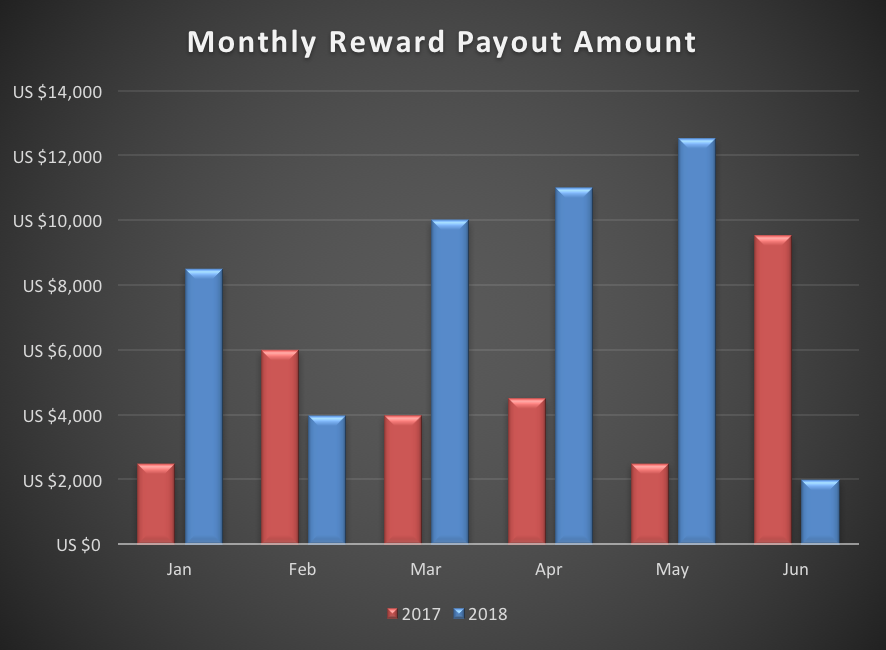
As mentioned earlier, we've updated our reward table. We will continue our efforts in improving our program to reduce security risks for LINE. Reporting vulnerabilities can be done anytime on the program's site and we look forward to having more participation from you all.
For those who'd like to find about the history of the program, see our previous posts:
For those who can read Japanese, have a look at the following articles too!
