About the LINE Security Bug Bounty Program
Hello, my name is Lee Myoung Jae (MJ) and I'm in charge of security at LINE. In this post I'm going to talk about the LINE Security Bug Bounty Program and the results of the program in 2016. The LINE Security Bug Bounty Program is an ongoing program to make the LINE app more secure for our users by letting external engineers submit bug (vulnerability) reports which we would then immediately fix.
We first conducted a trial run of the program called the LINE Bug Bounty Program from August 24 to September 23 in 2015. Based on our experience from that trial, we made various changes to create an improved bug bounty program for 2016. And on June 2, 2016, we launched the new and improved LINE Security Bug Bounty Program.
For more information about the LINE Bug Bounty Program, see our previous blog posts: "Introducing the LINE Bug Bounty Program" and "Results From the LINE Bug Bounty"
LINE Security Bug Bounty Program website: https://bugbounty.linecorp.com/
Bug report form: https://bugbounty.linecorp.com/apply/

Bug bounty FAQ: https://bugbounty.linecorp.com/en/faq/
Bug report submissions
We had a total of 97 bug reports filed during the seven months from June 2 to December 31, 2016. The charts below show the number of bug report submissions by week and the types of bug reports submitted.
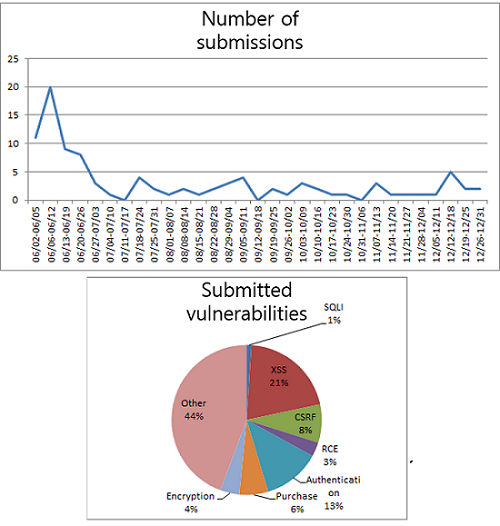
Weekly bug report submissions and type of bugs reported
Submissions by country
We received a total of 97 bug reports from 12 different countries. As you can see from the chart below, engineers from many different countries showed interest in our bug bounty program. As LINE continues to grow globally, we're also seeing an increased interest in the LINE Security Bug Bounty Program.
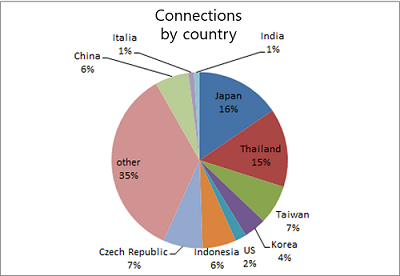
Submissions by country
Evaluation process
Submitted bug reports go through a 2-step evaluation process. Reports have to pass both the first and second evaluations to be recognized as a vulnerability. Once a bug report has passed the evaluation process, we give out the compensation (bounty) to the person who reported the bug and we add the reporter and the category of the vulnerability to our Hall of Fame which is open to public. For more details on the evaluation process, see our previous blog post.
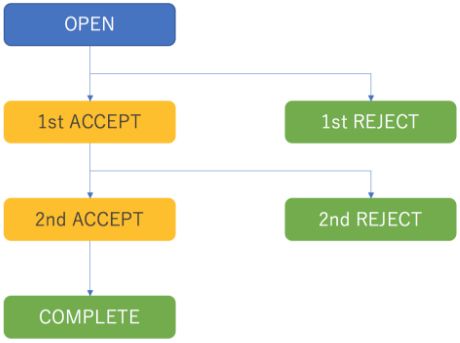
- 1st ACCEPT: Accepted for further evaluation
- 1st REJECT: Rejected for further evaluation
- 2nd ACCEPT: Bug is recognized as a vulnerability after conducting a detailed investigation
- 2nd REJECT: Bug is not recognized as a vulnerability after undergoing a detailed investigation
- COMPLETE: Compensation given
Results of the program
As a result of this bug bounty program, we found a total of 13 vulnerabilities which included cases of cross-site scripting (XSS) and cross-site request forgery (CSRF). In total, we gave out USD 27,000 in bounty in this program. You can take a look at the results on our Hall of Fame page. Updates to the Hall of Fame can be found on this page: https://linecorp.com/en/security/list/>https://linecorp.com/en/security/list/
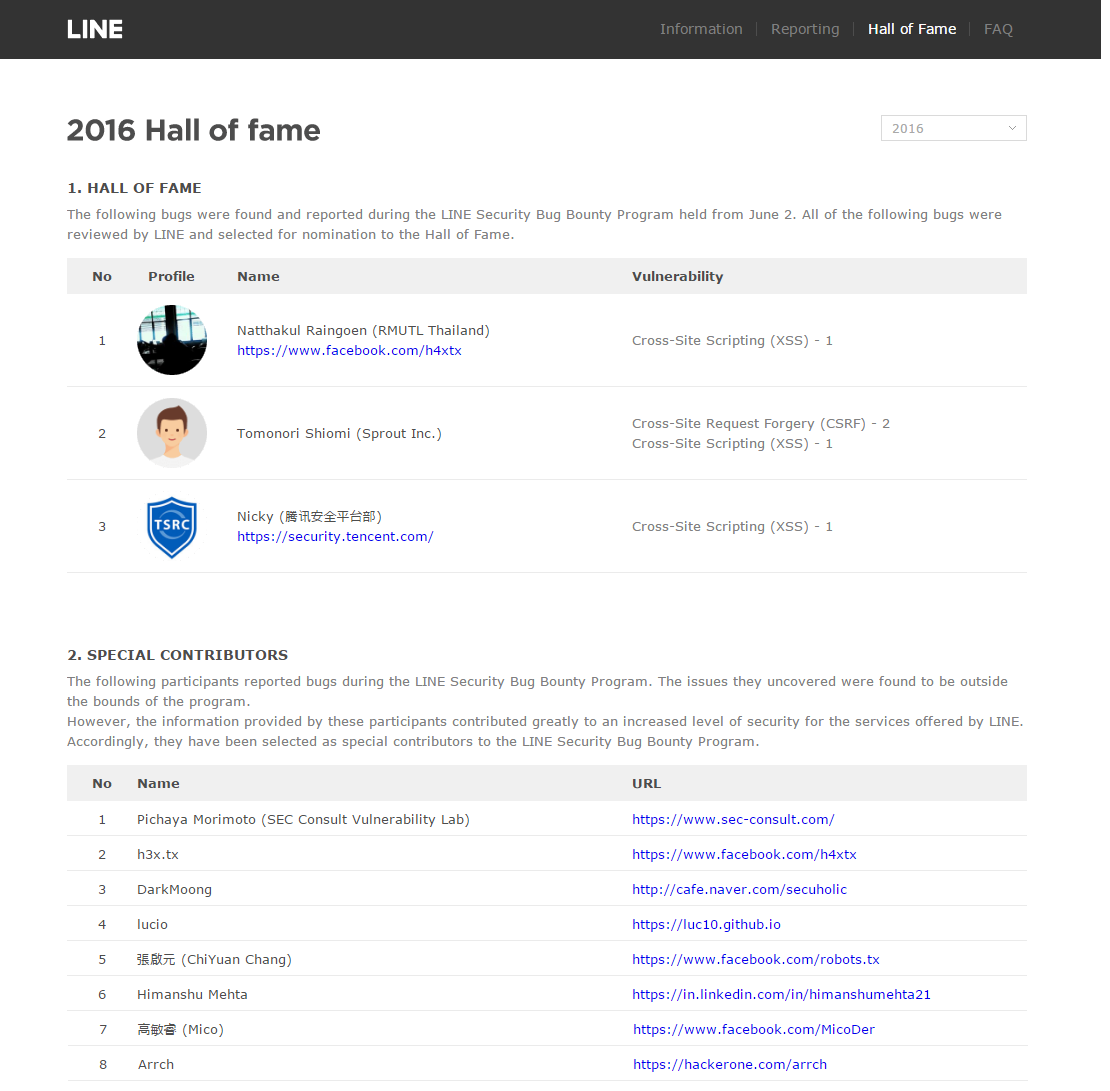
In addition, we recognized eight people as "special contributors" for the useful information provided in their bug reports even though they were not included in the Hall of Fame as their reports were not within the scope of the bug bounty program.
Ending notes
Because of the interest in the program and the reports we received, we were able to find several vulnerabilities. As we have taken measures to resolve the vulnerabilities, users can now use LINE more safely. We will continue to expand and develop the LINE Security Bug Bounty Program to further reduce the security risks at LINE. We appreciate your interest in this program and we're thinking of expanding the program as LINE is also increasing its number of services.
Also, you are welcome to report vulnerabilities at the LINE Security Bug Bounty Program site. Your participation is always appreciated.
